apt install postfix opendkimcfg files:
# This is a basic configuration for signing and verifying. It can easily be
# adapted to suit a basic installation. See opendkim.conf(5) and
# /usr/share/doc/opendkim/examples/opendkim.conf.sample for complete
# documentation of available configuration parameters
Syslog yes
LogResults no
LogWhy no
SyslogSuccess no
# Common signing and verification parameters. In Debian, the "From" header is
# oversigned, because it is often the identity key used by reputation systems
# and thus somewhat security sensitive.
Canonicalization relaxed/simple
Mode sv
SubDomains yes
OversignHeaders From
# Signing domain, selector, and key (required). For example, perform signing
# for domain "example.com" with selector "2020" (2020._domainkey.example.com),
# using the private key stored in /etc/dkimkeys/example.private. More granular
# setup options can be found in /usr/share/doc/opendkim/README.opendkim.
Domain hg-system.com
RequireSafeKeys False
Selector default
KeyFile refile:/etc/opendkim/keys/hg-system.com/default.private
KeyTAble refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
ExternalIgnoreList refile:/etc/opendkim/TrustedHosts
InternalHosts refile:/etc/opendkim/TrustedHosts
# In Debian, opendkim runs as user "opendkim". A umask of 007 is required when
# using a local socket with MTAs that access the socket as a non-privileged
# user (for example, Postfix). You may need to add user "postfix" to group
# "opendkim" in that case.
UserID opendkim
#Socket local:/var/spool/postfix/var/run/opendkim/opendkim.sock
#Socket local:/run/opendkim/opendkim.sock
#Socket "local:/var/run/opendkim/opendkim.sock"
PidFile /run/opendkim/opendkim.pid
Syslog Yes
TemporaryDirectory /run/opendkim
UMask 007
# Socket for the MTA connection (required). If the MTA is inside a chroot jail,
# it must be ensured that the socket is accessible. In Debian, Postfix runs in
# a chroot in /var/spool/postfix, therefore a Unix socket would have to be
# configured as shown on the last line below.
#Socket local:/run/opendkim/opendkim.sock
#Socket local:/var/run/opendkim/opendkim.sock
Socket inet:8891@localhost
#Socket inet:8891
#Socket local:/var/spool/postfix/opendkim/opendkim.sock
# Hosts for which to sign rather than verify, default is 127.0.0.1. See the
# OPERATION section of opendkim(8) for more information.
#InternalHosts 192.168.0.0/16, 10.0.0.0/8, 172.16.0.0/12
# The trust anchor enables DNSSEC. In Debian, the trust anchor file is provided
# by the package dns-root-data.
TrustAnchorFile /usr/share/dns/root.key
#Nameservers 127.0.0.1Code-Sprache: PHP (php)sudo nano /etc/opendkim.conf
# See /usr/share/postfix/main.cf.dist for a commented, more complete version
# Debian specific: Specifying a file name will cause the first
# line of that file to be used as the name. The Debian default
# is /etc/mailname.
#myorigin = /etc/mailname
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
readme_directory = no
# See http://www.postfix.org/COMPATIBILITY_README.html -- default to 3.6 on
# fresh installs.
compatibility_level = 3.6
# TLS, DNSSEC and DANE for SMTP client
#smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
#smtp_tls_security_level = dane
#smtp_dns_support_level = dnssec
# TLS parameters
#smtpd_tls_chain_files =
#/etc/letsencrypt/live/hg-system.com-0001/privkey.pem,
#/etc/letsencrypt/live/hg-system.com-0001/fullchain.pem
smtpd_tls_cert_file=/etc/letsencrypt/live/hg-system.com-0001/fullchain.pem
smtpd_tls_key_file=/etc/letsencrypt/live/hg-system.com-0001/privkey.pem
smtpd_tls_mandatory_ciphers = high
smtpd_tls_mandatory_exclude_ciphers = aNULL, MD5
smtpd_tls_security_level = encrypt
smtp_tls_policy_maps = hash:/etc/postfix/tls_polic
smtp_tls_CApath=/etc/ssl/certs
#smtpd_tls_ask_ccert = yes
#smtpd_tls_security_level = may
smtpd_tls_req_ccert = yes
smtpd_tls_auth_only = yes
# TLS, DNSSEC and DANE for SMTP client
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
#smtp_tls_security_level = dane
#smtp_dns_support_level = dnssec
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
myhostname = c1.hg-system.com
mydomain = hg-system.com
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = hg-system.com, c1.hg-system.com, localhost
relayhost =
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128 [2a02:1628:6005:6f00::]/60 5.231.137.19
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
inet_protocols = all
masquerade_domains = hg-system.com
maillog_file = /var/log/mail.log
virtual_alias_domains = hg-system.com
virtual_alias_maps = hash:/etc/postfix/virtual
#smtpd_milters = , inet:127.0.0.1:12768
#smtpd_milters = unix:/var/run/opendkim/opendkim.sock
#non_smtpd_milters = unix:/var/run/opendkim/opendkim.sock
# For use by dkim milter
#smtpd_milters = inet:localhost:8891
#non_smtpd_milters = $smtpd_milters
milter_default_action = accept
non_smtpd_milters = inet:localhost:8891, unix:/run/opendmarc/opendmarc.sock
#unix:/run/opendkim/opendkim.sock,
#unix:/run/opendmarc/opendmarc.sock
smtpd_milters = inet:localhost:8891, unix:/run/opendmarc/opendmarc.sock
#unix:/run/opendkim/opendkim.sock,
#unix:/run/opendmarc/opendmarc.sock
milter_protocol = 6
#smtpd_milters = inet:127.0.0.1:8891
#non_smtpd_milters = inet:127.0.0.1:8891
#non_smtpd_milters = $smtpd_milters milter_default_action = accept
#smtpd_milters = inet:localhost:12768 unix var/spool/postfix/ctmilter/ctmilter.sock
#non_smtpd_milters = inet:localhost:12768 unix var/spool/postfix/ctmilter/ctmilter.sock
#smtpd_milters = unix:/var/run/opendkim/opendkim.sock
#non_smtpd_milters = unix:/var/run/opendkim/opendkim.sock
#smtpd_milters = inet:localhost:12768
#non_smtpd_milters = inet:localhost:12768Code-Sprache: PHP (php)nano /etc/postfix/main.cf
CATCH-ALL
nano /etc/postfix/main.cf
<span style="text-wrap: wrap;">virtual_alias_domains = mydomain.tld</span>
<span style="text-wrap: wrap;">virtual_alias_maps = hash:/etc/postfix/virtual</span>Code-Sprache: HTML, XML (xml)nano /etc/postfix/virtual
@mydomain.tld name@gmail.comCode-Sprache: CSS (css)postmap /etc/postfix/virtualservice
postfix reload
Nach jeder Änderung muss ein postmap durchgeführt werden, damit Postfix die Änderung mitbekommt
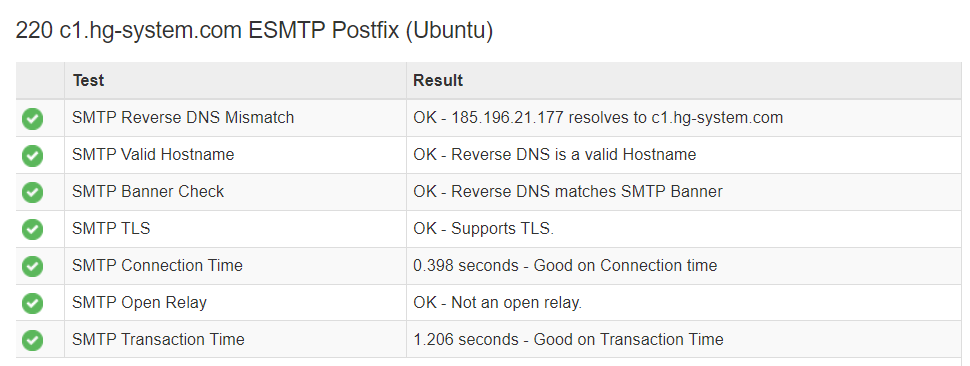
Check Config with Online Tool
https://mxtoolbox.com/SuperTool.aspx?action=smtp%3ahg-system.com&run=toolpage